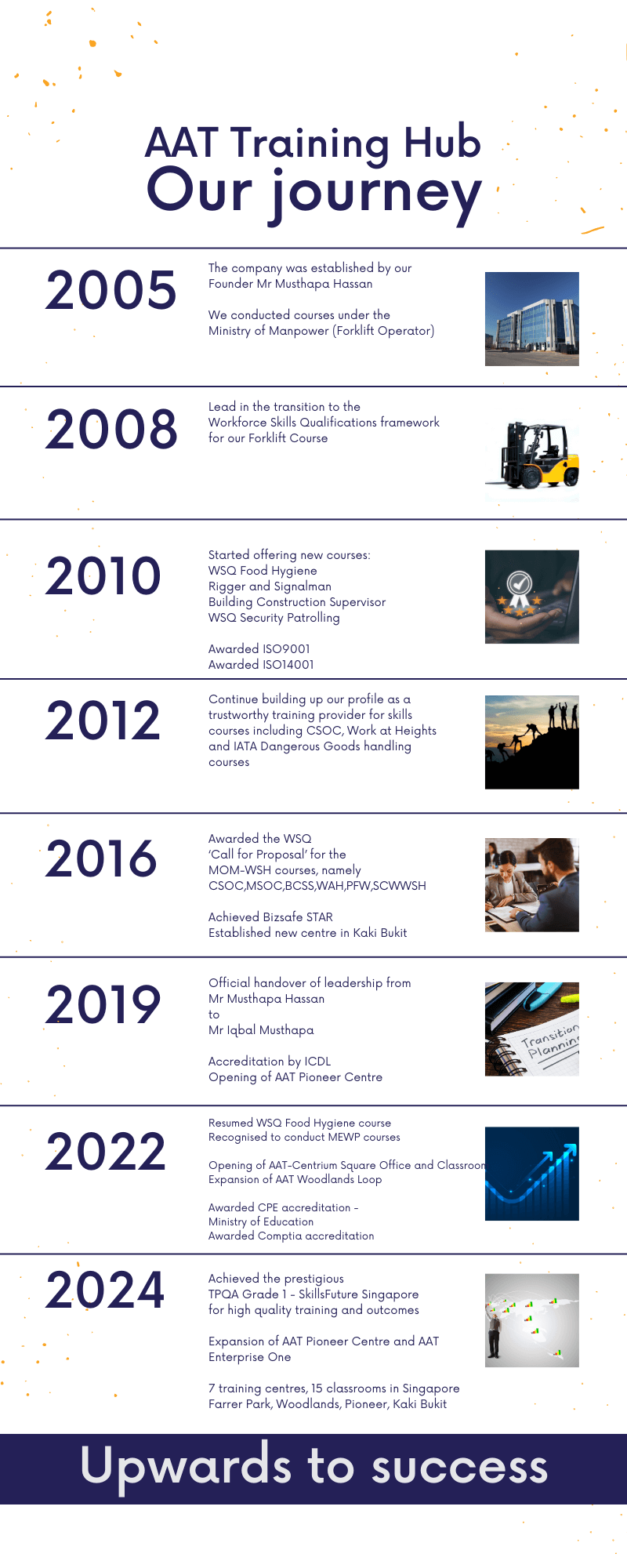
Ad Victoria Supra – Upward to Success
Our motto embodies the spirit of ambition and excellence. We are dedicated to fostering an environment where both our organization and our students consistently strive for success. Guided by our expertise, we inspire learners to achieve their fullest potential in every aspect of their educational journey.
AAT Training Hub is a leading educational institution committed to delivering holistic learning experiences through a competency-based curriculum. Leveraging advanced educational technologies, we aim to create impactful programs tailored to learners of all levels.
As part of our vision, we uphold the highest standards in training by implementing accredited procedures and applying proven methodologies. We are proud to be certified under ISO 45001 and ISO 29990 standards and recognized as a BizSafe STAR organization, demonstrating our dedication to quality, safety, and excellence.
To deliver innovative, technology-driven, and holistic learning programs through a competency-based curriculum that empowers learners to achieve their goals.
To be a pioneering educational institution that inspires students to excel and achieve unparalleled success, utilizing innovative technology and fostering a culture of excellence in competency-based education.
AAT Training Hub Pte Ltd is registered with the Committee for Private Education (CPE) under the SkillsFuture Singapore Agency as a Private Education Institution. This registration is governed by the Singapore Private Education Act (2009).
CPE Registration Number: 200503548R